
Several anti-spam solutions exist on Drupal to prevent the submission of forms (contact, newsletter subscription, etc.) by more or less well-intentioned robots. Without wanting to be exhaustive, we can use the Honeypot and Antibot modules which provide (different) non-intrusive defence mechanisms, or the captcha / recaptcha modules which ask the visitor to respond to different challenges before allowing him to submit the form.
But these anti-spam modules are not infallible and some robots can sometimes override their protection mechanism. They can then turn your site into a relay for unsolicited email, via your contact form for example, which will send a confirmation email to the email entered on the form. In the worst case, your site can start sending thousands of e-mails per hour for various or varied advertisements, until your host announces that it has blocked your server.
To avoid this kind of situation, and to end up with a domain name blacklisted by the mail relays, we can use a last line of defence, behind the anti-spams enabled, which can (almost) certainly block and limit this type of attack very strongly. The Protect Form Flood Control module will allow us to control the number of submissions allowed within a defined time window for a given IP address. And this for any form on a site.
Its operation is quite simple and consists of applying, on all available forms, the same protection system that Drupal Core uses for forms related to authentication on a Drupal site in order to counter brute force attacks on passwords.
Once the module is enabled, its configuration can be done quickly in a general way, with the possibility of refining certain control parameters (threshold and time window) form by form.
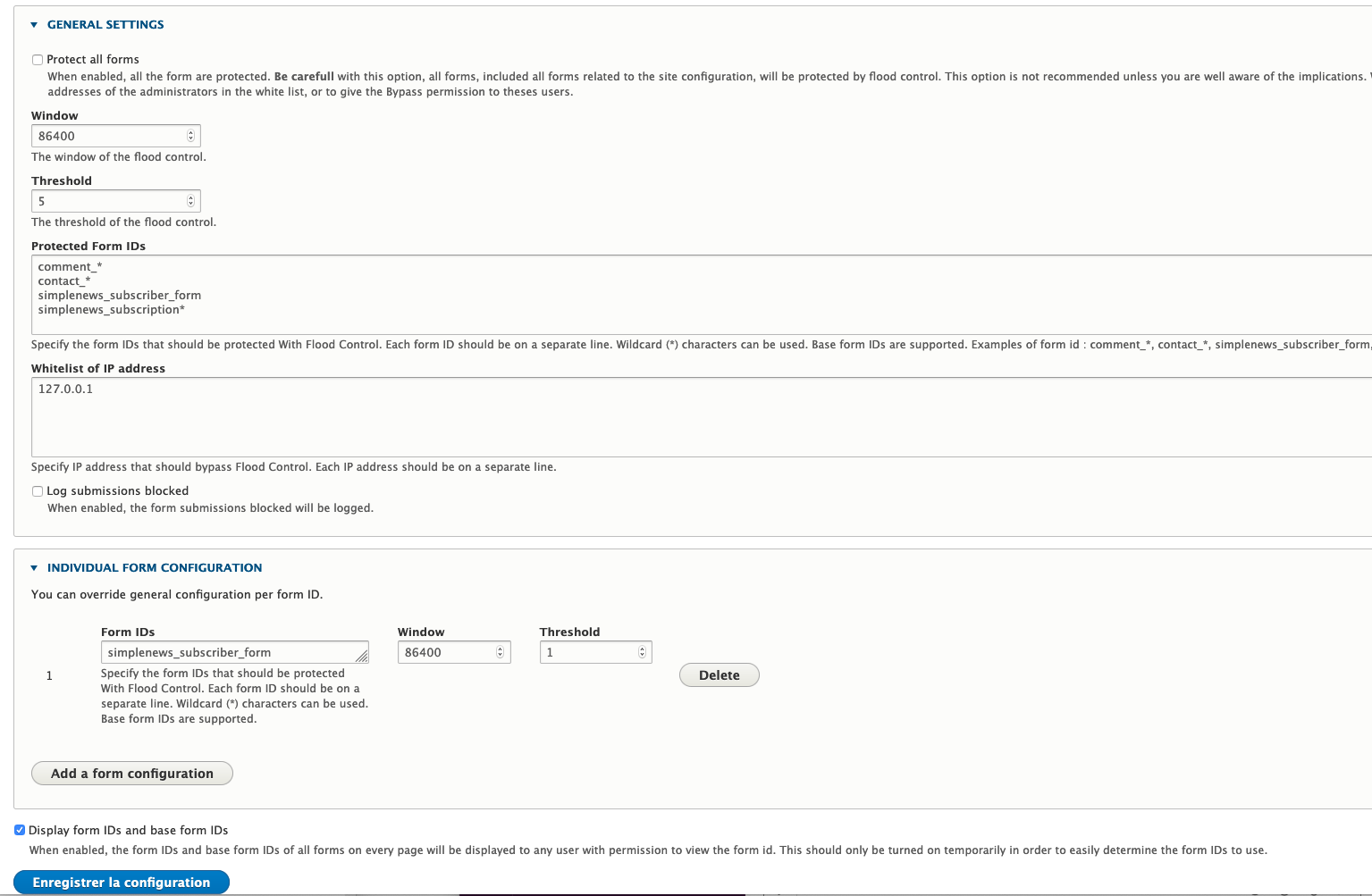
You can configure the following settings:
Protect all forms
When this option is enabled, all forms are protected. Be careful with this option, all forms, including all forms related to site configuration, will be protected against bulk submissions. This option is not recommended unless you fully understand the implications. With this option enabled, it is strongly recommended that you set the IP addresses of administrators, whitelisted or give "Bypass Protect Form Flood Control" permission to these users.
Window
The time window for checking mass bids.
Threshold
Form submissions that exceed this threshold, during the time window defined above for an IP address, will be blocked.
Protected form identifiers
Here you specify the form identifiers that must be protected against bulk submissions. Each form identifier must appear on a separate line. Wildcards (*) may be used. The form_id or base_form_id can be used.
Unprotected form identifiers
If the Protect all forms option is checked, you can configure form identifiers that should NOT be protected against bulk submissions.
IP Address WhiteList
You can set whitelist IP addresses, IP addresses that can bypass the mass submission control .
Logging of blocked submissions
When this option is enabled, blocked form submissions are recorded in the activity logs.
Individual settings
The module also allows Threshold and Window settings to be configured individually for certain forms. The individual settings set then take precedence over the general settings and will be applied instead of the general settings.
Finally, an option allows you to trigger a window on any page containing a form that displays their identifiers in order to configure the module more easily.
To conclude, there is not really an ideal configuration. The right settings will have to be made according to the typology of visitors to the Drupal site. In particular, taking into account the fact that visitors (likely to submit a form) come from a company network, and therefore probably behind a proxy, or not. Having intervened urgently over the last six months, as a Drupal expert, on three Drupal projects having suffered this type of attack (spam relay via the contact form), this module should make it possible to considerably reduce their scope.

Ajouter un commentaire